This is a five-part series independently produced and investigated by Spacing
At some point in mid-2020, with the pandemic raging, the Toronto Public Library began working with the Gartner Group, a large U.S. research and IT consulting firm, to re-launch the TPL’s 2020-2024 Digital Strategy, work on which had been sidelined by the lockdown.
Tucked into the TPL’s broader strategic plan, the new program — unveiled with a certain amount of bureaucratic fanfare in January, 2021 and subsequently approved by the TPL board — came fitted out with all sorts of promises cast in the impenetrable jargon of the tech world: “consistent customer experiences across channels of engagement” meant to “drive” customer satisfaction; “redesigned or new functional capabilities”; “optimization” intended to improve “productivity” of front line staff, and so on. It was all dubbed “a journey of reinvention.”
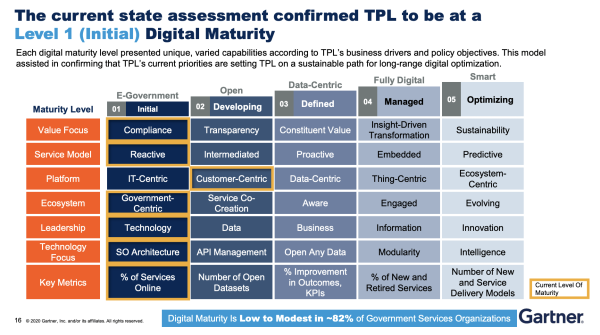
“Gartner leveraged industry best practices and conducted a number of assessments, workshops and interviews,” the staff report noted, all presumably with the goal of providing TPL with a menu of assessments and reports and more consulting opportunities. Among these was one on the library’s so-called “digital maturity” level, which Gartner assessed to be at level one (out of five possible levels) — a widely used metric in the cybersecurity world that denotes preparedness against external threats. (A graphic of the National Institutes for Standards and Technology “maturity model” is on page 29 of the TPL’s digital strategy presentation.)
The staff report, likely repeating a claim from Gartner, stated reassuringly that 80% of government services have low to modest digital maturity levels. “Essential to improving TPL’s digital maturity and overall success are redesigned or new functional capabilities and innovation, speed and agility,” it stated. “So Gartner recommended that the focus of TPL’s Digital journey be on optimization and setting the stage for transformation.” In particular, it laid out a timeline to bolster the TPL’s cybersecurity systems that would run from 2021 to 2023. But the strategy made no mention at all of preparing for ransomware attacks.
Toronto’s Auditor General was less sanguine and certainly less patient. In a strongly worded June, 2021, warning released less than half a year after the TPL’s revamped digital strategy, former TAG Beverly Romeo-Beehler told City officials and City agencies to sharply accelerate preparations for high-risk events, and specifically ransomware attacks.
Quoting risk assessments from the so-called Five Eyes and the U.S. Department of Homeland Security, among others, as well as examples of recent debilitating attacks on critical infrastructure, Romeo-Beehler said there’s an urgent need for the City to pick up the pace. “The outcomes of a cyberattack can be devastating to the City,” she wrote, noting in particular the risk that municipal agencies wouldn’t be able to deliver services and could lose control over sensitive or confidential personnel information.
Her stern warning went out to City officials fully two years before the TPL attack.
In May, 2022, Romeo-Beehler’s office released an update, which involved a review of publicly available information on the progress of the cyber-security improvements being carried out by the City and a handful of Toronto agencies, including the TPL. Her office provided each of the listed agencies, including TPL, with specific recommendations on what still needed to be done, but these weren’t made public (most information on cyber-security vulnerabilities and preparedness is kept strictly confidential for all the obvious reasons).
In an email to Spacing, the current auditor general, Tara Anderson, said her office had subsequently checked in with TPL to see how it had progressed. “We did the follow-up on those recommendations that were reported by management as fully implemented as of December 2022,” she wrote. “I’m not able to provide further information given it is confidential.”
Just over a year before the attack, TPL chief librarian Vickery Bowles, issued a short report updating the annual “risk register” — a bucket of 27 metrics meant to gauge internal and external IT risk, and which has been in use since 2018. Without providing details, Bowles said six of the 27 risks had “increased,” two had declined and the balance remained unchanged.
(In December 2023, two months after the attack, the TPL updated its risk register evaluation in a report to the board. Library officials revealed that they had adopted a new way of measuring risk — “a revised format that matches industry standards” — along 24, instead of 27, categories or metrics. In eight of the 24, the current risk level scores were found to be “extreme” or “high,” while the remaining 16 were scored as low, medium or medium-high; the report provided no further breakdown. TPL board members were given more details about these scores, but that information was not made public.)
It’s not particularly clear from the public record how much progress TPL made during 2022 in terms of battening down its cybersecurity risks and fostering a culture of vigilance among its far-flung employees. One change that did come into effect was annual mandatory staff training, which was introduced for the first time in 2022. The 60- to 90-minute sessions included guidance on compromises emails, phishing, cloud security, remote work and safe passwords. (The TPL has reported that in 2022, 3% of TPL’s staff were “successfully phished.”)
One TPL branch manager describes the first round of cyber-security training sessions as ” very much an off-the-shelf product that didn’t actually match our working environment as much as it could. [It] was very much there so that the organization could say that they’ve done this thing.” The second round, this person adds, was “considerably better.”
“Anecdotally,” Brandon Haynes, president of CUPE Local 4989, which represents the library workers, “I will tell you that I have heard feedback from people that are not satisfied with the level of training related to cybersecurity, probably as a result of different conversations at the City over the last few years that there was a mandatory cybersecurity training that people are required to attend.” He continues: “The feedback that I hear from people is that they struggle to get time away from their regular duties.”
TPL spokesperson Ana-Maria Critchley stated in an email that TPL had mandatory training in place prior to the ransomware attack but added, “In addition to existing TPL training, we are investigating the cyber training offered through the Office of the Chief Information Security Officer at the City of Toronto.”
As for all the other fixes required by both the auditor-general and the City’s IT officials, the TPL’s last major progress report issued before the ransomware attack suggests, with the benefit of hindsight, a work that was very much in progress. According to a chart in that March, 2023, document, the City of Toronto’s IT division had identified 13 security controls that the TPL needed to implement as part of its overall cyber-security preparedness. Five, however, had yet to be completed. These included: “remediating all critical, high and medium security patches”; putting in place complex passwords in all systems; imposing tight controls on all administrative systems; properly controlling all network access; and putting in place disaster recovery plans.
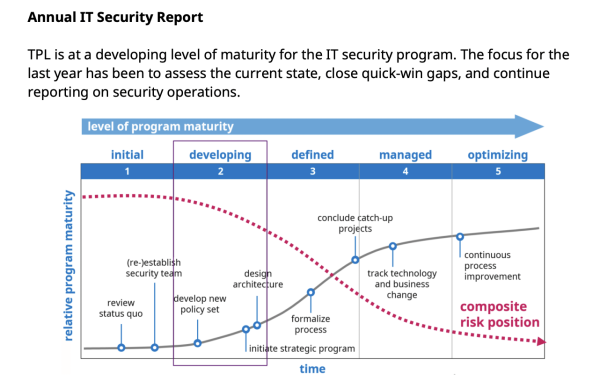
As the report stated, TPL’s systems had advanced to a maturity level two (out of five), also known as “developing” — a state of preparedness common among governments. A chart in the document depicting the evolution of a fully-fleshed out cybersecurity system shows a pair of lines: one in black that’s trending up, indicating progress with the deployment of various security measures, and the other — in red — trending down, showing the level of risk over time.
According to TMU cybersecurity expert Charles Finlay, the TPL’s assessment of its own security preparedness viz other public sector entities “is likely correct, but this is not a situation we can simply accept. All of us — including governments at all levels, the private sector, the academic community, and the public sector — must work hard to build cybersecurity capacity across the public sector in Canada. The safe functioning of our society and economy relies on our public institutions rapidly reaching an optimized level of cybersecurity maturity.”
In an email, TPL spokesperson Critchley said that the March, 2023, report referenced “initiatives underway…at the time this report was authored. These initiatives include Updated Password Standards, Multi-Factor Authentication, Response & Recovery from Cyber Security Incidents and Vulnerability Management Program. All of these initiatives were either completed or underway at the time of the cybersecurity incident.”
However, the “you-are-here” box on the chart (above) offers a bracing snapshot of the TPL’s preparedness circa the spring of last year. The red risk line was still well above the one plotting progress. The TPL’s lengthy to-do list — everything from phishing risk assessments to the development of disaster and recovery plans — suggested much to be done. “By maintaining and improving policy, practices and technology,” the report states in a tone of studied bureaucratic calm, “the risk of internal and external cyber security threats are minimized.”
Black Basta struck almost exactly seven months later.
Part I: Toronto Public Library ransomware attack: Overview
Part II: Toronto Public Library ransomware attack: Unanswered Questions
Part III: Toronto Public Library ransomware attack: Was TPL adequately prepared to defend itself?
Part IV: Toronto Public Library ransomware attack: Where does the TPL go from here?
Part V: Q+A with Toronto’s chief librarian, Vickery Bowles